AWS Identity and
Access Management in action (Basics)
Author: Donatien MBADI OUM, Oracle |
AWS | Azure
1.
What is IAM?
AWS IAM Overview
AWS Identity and Access Management or IAM is a service that allows AWS
customers to manage user access and permission for their accounts, APIs at a
service level or resource level within AWS.
IAM can manage users and security credentials (such as API access keys) and
allow users to access AWS resources such as EC2, S3 etc.
With IAM, you can specify Who or What Can access services and resources in
AWS, centrally manage fine-grained permissions and analyze access to refine permissions
across AWS, whether through the AWS GUI-based console in a web browser or
through the AWS command line interface (CLI) or different Software Development
Kits (SDK).
Let’s walking through the basic functions of IAM in practice, focusing on
user and group management and assigning access to the specific resources using
IAM-managed policies.
2.
IAM Users, Groups, Roles and Policies
When you first create an AWS account, you begin with one sign-in identity
that has full access to all AWS services and resources in the account. This identity
is called a Root user and is accessed
by signing in with the email address and password that you used to create the
account.
We strongly recommend that you secure and don’t use the root user for day-to-day
tasks. Your root user credentials must be used to perform the tasks that only
the root user can perform. To secure the root account, you can:
-
Enable multi-factor authentication
-
Create an admin group for your
administrators, and assign the appropriate permissions to this group
-
Create user accounts for
administrators
-
Add user to the admin group
An IAM user is an identity within your AWS account that has specific
permissions for a single person or application.
An IAM group is an identity that specifies a collection of IAM users. Groups
is used to specify permissions for multiple users at a time.
In the above diagram, we have an AWS accounts. Inside IAM, we create
different groups, and users can belong to those groups. For example, Mbadi and
Mohamadou might belong to the group Admins which provide different sets of
permissions such as access to billing or access to managing other IAM users,
roles, policies or other security information. Group Developers might only have
access to a subset of services such as a set of EC2 instances of specific S3
buckets that allow Boyomo, Kenfack, Foundike and Tia to write development code
for their applications. Group Test might have a different set of access that
allow Fadimatou, Santounga and Assouala to make application testing.
An IAM role is an identity within your AWS account that has specific
permissions. A role is similar to a user, but it is not associated with a
specific person.
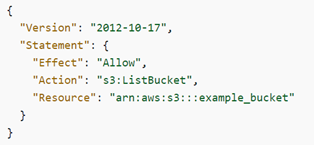
A policy is an object in AWS that, when associated with an identity or
resource, defines their permissions. AWS evaluates these policies when an IAM
principal (user or role) makes a request. Most of policies are stored in AWS as
JSON documents. You can create your own policy or use existing policies.
Example of JSON Policy
-
Version – specify the version of the policy
-
Statement – use as container for the following
element
-
Sid – (Optional) – Include statement ID to
differentiate between your statements
-
Effect – Use Allow or Deny to indicate
whether the policy allows or denies access
-
Principal – (Required only for some circumstances),
Implies user or role
-
Action – Include a list of actions that the
policy allows or denies
-
Resource - (Required only for some circumstances),
Specifies the list of resources
-
Condition – (Optional), Specifies the
circumstances under which the policy grants permission
3.
Lab presentation
In this lab, we will walking through the basic
functions of IAM, focusing on user and group management and assigning access to
specific resources using IAM-managed policies. We will how to find the login
URL for AWS users to be able to log into the account. We will log in different
AWS users and see how different permissions that are assigned via the groups
affect the users.
|
User |
In Group |
Permissions |
|
user1 |
S3Support |
Read-Only access to S3 |
|
user2 |
EC2Support |
Read-Only access to EC2 |
|
user3 |
EC2Admin |
View, Start, Stop EC2 instances |
Three groups will be created. The first is the S3 Support group which
provide read-only access to S3. EC2 Support group which provides read-only
access to EC2 and the EC2 Admin group which provides permissions to view, start
and stop EC2 instances. Three users will be created, user1, user2 and user3
which belong respectively to S3 Support group, EC2 Support group and EC2 Admin
group.
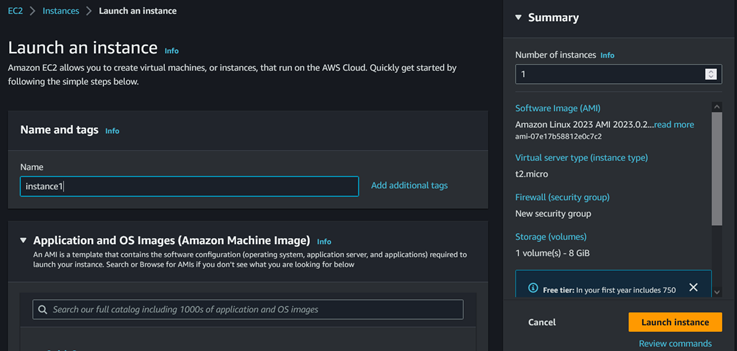
3.1. Create a EC2 instance
a.
Log
in to the AWS Management Console using your root account.
b.
Navigate
on EC2, click in Instances and Launch instances
c.
Enter instance name and Proceed
without a key pair, Leave others on default values en click on Launch Instance
d.
The instance is successfully created
3.2. Create a policy
Log in to the AWS Management Console using your
root account.
a.
Navigate on Policies and Click on
Create policy
b.
Define permissions
On Visual Editor Tab, click on Choose a service and add
actions and click on Next tags
c.
Review policy
Enter a policy name and click on Create policy.
d.
Explore a JSON policy
3.3. Group creation
a.
Log
in to the AWS Management Console using your root account.
b.
Navigate to IAM
c.
Click on User Groups and then Create
group
d.
Enter a group name and attach the
policy
For the other groups, S3Support and EC2Support we will use existing AmazonS3ReadOnlyAccess and AmazonEC2ReadOnlyAccess policies
respectively.
3.4. User creation
a.
Log
in to the AWS Management Console using either your root account.
b.
Navigate
on IAM, Click user, Add users
c.
Enter
user name and Click on Next
d.
Set
permissions
Add user to group and Click Next
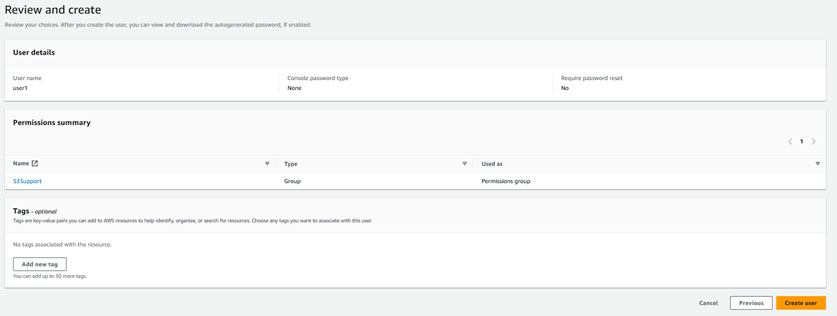
e.
Review
and create
Click on Create user
e.
Enable user to have console access
Click on a user name and on Enable console access
f.
Choose Enable option button et
optionally define a custom password
g.
Apply changes
f.
Repeat the same procedure for user2 on
EC2Support group and user3 on EC2Admin group.
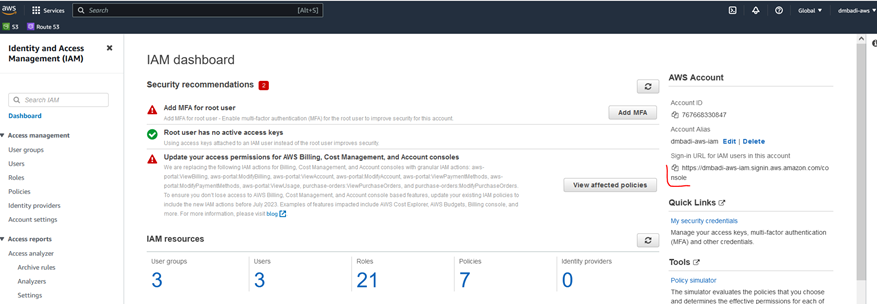
3.5. Use the IAM Sign Link to Sign in as
Each user
In the
IAM sidebar menu, select Dashboard
In the AWS
Account section on the right, copy the sign-in URL
3.5.1. Sign in as user1
a.
In a new browser tab, navigate to the
URL and log in to AWS Management Console as user1
b.
By remembering that this user only has
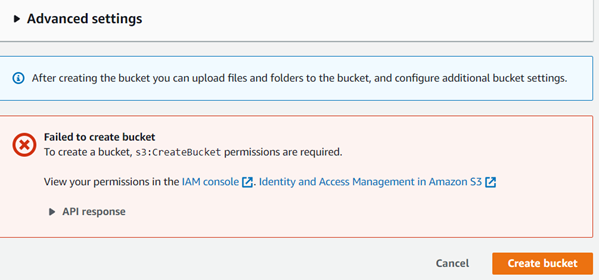
read-only access to S3. Navigate on S3 and Click on Create bucket
c.
Enter bucket name
d.
Leave all other default settings and
click Create bucket
You should receive an Access Denied error, indicating
that your group policy is in effet
e.
Navigate on EC2. You should see a
number of API errors, indicating that you do not have access to EC2.
f.
In the top right corner of the page,
expand the user1 dropdown menu and copy the Account ID and then click Sign out.
3.5.2. Sign in as user2
a.
Remember that this user only has
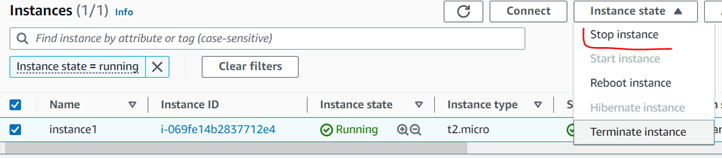
read-only access to EC2. Navigate on EC2. Select Instances (running)
b.
Check the checkbox to the left of the
running instance and review the instance details
c.
Along the top of the page, use the
instance state dropdown to select Stop instance, and then click Stop
You should see an error message, since
this user doesn’t have the permissions to stop instances
d.
Navigate to S3. You should see that S3
is unavailable for user2 because this user doesn’t have any permissions outside
of EC2.
Copy the Account ID and then Sign out.
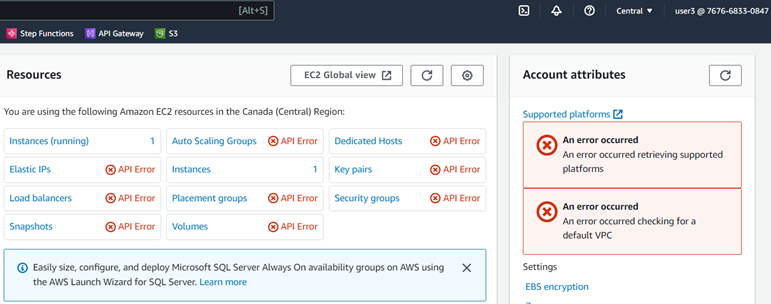
3.5.3. Sign in as user3
a.
Remember that this user can view,
start and stop EC2 instances. Navigate on EC2. From resources section, select
Instances (running)
b.
Check the checkbox to the left of the
running instance, use the instance state dropdown to select Stop Instance, and
then click Stop.
c.
You can see that the instance is in
Stopping state
d.
After a minute, refresh the instances
page to verify that the instance is now in a Stopped state.


































Aucun commentaire:
Enregistrer un commentaire